
Data diode technology: An approach to improving both the security and interoperability of your manufacturing systems
May 2, 2011
By Joost Bijl
From the viewpoint of national security, more manufacturing processes than you would think fall into the category of “critical manufacturing.” The U.S. Department of Homeland Security, for example, identifies nine manufacturing areas as critical infrastructure, including iron and steel mills; ferrous and nonferrous metal processing; and the manufacturing of machinery, electrical equipment and transportation equipment. Public Safety Canada also identifies manufacturing as one of 10 critical infrastructure sectors, and collaborates with the United States on a cross-border approach to information sharing and protection through initiatives such as the “Canada-United States Action Plan for Critical Infrastructure.”
Any disruption in a manufacturing process has a ripple effect downstream. Even if you don’t consider your type of manufacturing part of critical infrastructure, you’re more than likely a not-too-distant relative and, therefore, have a responsibility to protect your process networks from security breaches.
Why you should worry about security
A security breach of your process control network can be catastrophic – not only to your company, but to your customers, business partners and, depending on your type of business, an entire population. For reasons of espionage, terrorism, extortion or just vandalism (such as retribution from a disgruntled worker), adversaries have their reasons to penetrate your network.
Malware can be designed to steal proprietary information, disrupt processes or even take over control of processes. According to Internet security studies by firms like McAfee and PandaLabs, tens of thousands of new malware strains are introduced every day. Unlike the mischief engaged by early hackers, malware today is a business complete with “how to” websites and is increasingly designed to harm.
Two well-publicized penetrations of process control networks within the last year – the Stuxnet worm and Night Dragon attacks – exposed a feared but clear trend toward the weaponizing of malware by governments, terrorists and virtually any group committed to achieving an objective. In today’s world, lines of malicious code can sometimes accomplish what traditional espionage, weaponry and diplomacy can’t.
The conflict between systems interoperability and information security
Against this backdrop, manufacturers seek to integrate systems across their extended enterprise to obtain optimal levels of business performance. This includes information sharing between process control networks and less secure back-office systems to improve business visibility and decision making. At the same time, data and the programming that controls manufacturing processes must be protected against increasingly sophisticated cyber threats.
Even when fully compliant with, for example, the latest OPC standards, security measures for process control networks are limited to Distributed Component Object Model-based (DCOM) access permissions, firewalls and “air gap” data transfers, which are vulnerable to human error and malicious intent. Firewalls and access permissions to sensitive systems can be wrongly configured. Devices used for air gap data transfer – such as USB flash drives – can be misplaced, stolen or infected with malware and transferred to a critical network, intentionally or accidentally. (The Stuxnet worm used to target SCADA systems can initially infect networks through air gap devices, according to the experts who disassembled the code.)
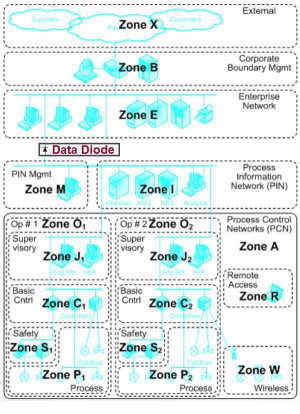
How data diode technology improves both security and systems interoperability
A data diode is a protection system that allows data to be sent from your process control network for information updates, but physically prevents electronic access to that network. Just as a diode in basic electronics allows current to flow in only one direction, data diode technology allows data to flow safely in one direction to connect the sensitive part of your infrastructure with less secure systems and networks.
Data diode systems do not contain decision logic, software or firmware that could compromise ICS (Internet connection sharing) architecture. They eliminate opportunities for software malfunctions, malware, tampering and online attacks. They cannot be configured incorrectly, eliminating the potential for human error.
This technology can be implemented at SCADA servers that connect data from PLCs, RTUs, sensors, valves, scales, analysers, distributed control systems and improvised devices for systems interoperability across your process network. It improves systems interoperability between your process network and back-office systems by eliminating the delays in information transfer associated with air gap procedures, which are neither continuous nor real time.
Process data can be fed directly to less-secure information management systems in real time for up-to-date business visibility and decision making affecting financial, operational and customer service performance – without exposing your process network to cyber threats.
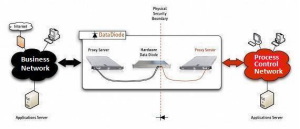
How data diode technology works
Data diode technology is comprised of three elements – a hardware data diode, proxy servers and software for data integrity (error detection and correction); data transfer synchronization, event logging and simple network management protocol traps (on both sides of the data transfer); and a user interface for administrators and security auditors.
A one-way physical connection is made between the two servers to prevent data leakage and guarantee the protection of the process control network. Each server has an easy-to-use web interface that allows authorized users to configure what information is to be transferred. As the physical connection between networks is one-way (hardware), malware will never compromise the process control network. One data diode can support transfers from multiple SCADA servers. The basic solution can be augmented with additional application servers to add specific functionality to the one-way data transfer.
Strengthening your overall defence-in-depth strategy
Some companies offer data diode technology as another layer of security for manufacturers’ overall defence-in-depth strategies. When used with advanced server software, data diode technology supports complete control over information browsing, reading and writing on a per-user, per-access basis in manufacturing environments. Instead of relying only on global, DCOM-based, “all-or-nothing” system access permissions, manufacturers can have granular, role-based access control to prevent unauthorized access to process data and programming controls, whether accidental or intentional.
Joost Bijl is marketing manager for cyber defence specialist Fox-IT and is a Certified Information Systems Security Professional (CISSP).
Advertisement
- Industrial wireless network management system
- Chrysler turns first profit since its bankruptcy, thanks to growing sales